Compliance Check
Before a Managed OS v2 VM can go into the Full Managed state, compliance checks must be run. Only if all relevant checks are successfully passed, the VM will be transferred to the respective state. If one or more tests are not successful, then this must be corrected by the customer. Afterwards the state change can be requested again.
The compliance check will be executed when the following state changes are requested:
- Temp Admin to Customer Maintenance
- Temp Admin to Full Managed
Compliance Checks for Managed Windows
This section describes the checks to be executed before offering the Full Managed service on a given system.
| ID | Test case | Expected results & How to fix it |
|---|---|---|
| Base.AdminAutologon.Tests | Testing if automatic logon for Admins is disabled | Automatic logon should be disabled. If failed, use the following powershell command to reset it: Set-ItemProperty -Path 'HKLM:\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon' -Name "AutoAdminLogon" -Value 0 |
| Base.Administrators.Tests | Testing local Administrators membership | Local Administrators should have only swisscom-allowed accounts as member Please remove any added users from Administrators group and follow user management procedure to give access: https://docs.entcloud.swisscom.com/guide/managed-services/managed-os-win/how-to/user-management/ |
| Base.AdminPrivilege.Tests | Testing Administrators Privileges | Local Administrators Group must have the following Privileges: - Access this computer from the network - Allow log on locally - Allow log on through Terminal Services If failed, please confirm and re-add group Administrators to the privileges above by: Run secpol.msc, navigate to Security Settings/Local Policies/User Rights AssignmentIn the list of privileges, find each of the above. Make sure Administrators is member of all 3. |
| Base.AuditPolicy.Tests | Testing if Audit Policies are configured to audit Success and Failure | The following Audit Policies are configured to audit Success and Failure: - Logon - Logoff - Account Lockout - IPsec Main Mode - IPsec Quick Mode - IPsec Extended Mode - Special Logon - Other Logon/Logoff Events - Network Policy Server - User / Device Claims - Non Sensitive Privilege Use - Other Privilege Use Events - Sensitive Privilege Use - Authentication Policy Change - Authorization Policy Change - MPSSVC Rule-Level Policy Change - Filtering Platform Policy Change - Other Policy Change Events - Audit Policy Change - User Account Management - Computer Account Management - Security Group Management - Distribution Group Management - Application Group Management - Other Account Management Events - Kerberos Service Ticket Operations - Other Account Logon Events - Kerberos Authentication Service - Credential Validation If test failing, please check the error message, which policy is causing trouble To get all Audit policies, please use the following command: auditpol.exe /get /category:*The failing audit item should not be set to audit Success and Failure To set one item audit for success and failure, please use the following command (Replace {FAILING_NAME_HERE} with correct policy item): auditpol.exe /set /subcategory:{FAILING_NAME_HERE} /success:enable /failure:enableFor example, let's say that Logon policy is not set correctly, to set it to audit both success and failure, the following command should be used: auditpol.exe /set /subcategory:Logon /success:enable /failure:enable |
| Base.BitLockerDriveEncryption.Tests | Testing if the WindowsFeature Bitlocker is installed | The Bitlocker should not be installed on the local the machine. In case of failure, please first ensure that no disks are encrypted on the system. This can be done by running command manage-bde -status!!! Only after confirming that there are no encrypted disks on the system !!! Bitlocker can be removed by running the following command: Uninstall-WindowsFeature -Name Bitlocker |
| Base.BITSService.Tests | Testing BITS Service StartMode | The BITS Service should not be disabled To enable service, please set it to Manual startup (default): Set-Service BITS -StartupType Manual |
| Base.BuiltInAccountsDisabled.Tests | Testing if Built-in Accounts are disabled | The Built-in Administrator should be enabled To enable Built-in Administrator, please run the following powershell command Get-LocalUser | where {$\_.sid -like 'S-1-5-\*-500'} | Enable-LocalUserThe Built-in Guest should be disabled To disable guest, please run the following powershell command Get-LocalUser | where {$\_.sid -like 'S-1-5-\*-501'} | Disable-LocalUser |
| Base.ComputernameChanged.Tests | Testing if the Computername changed | The computer name should not have changed since it is registered in the cloud management systems. Please set the computer name to the original name by running Rename-Computer powershell command. You will be prompted for new computer name, which should be the name as set when machine has been created. |
| Base.CpuUsage.Tests | Testing CPU load average | The average CPU usage should be less than 95 Percent. Please ensure there are no application overloading the CPU or increase number of CPU cores if required (pleas use day 2 action "Reconfigure" once the server it's in Customer Maintenance Mode). |
| Base.DeviceManager.Tests | Testing Device Manager for errors | The Device Manager should not return any errors. Please open device manager and make sure there are no failing or problematic devices. There should be no problem as long as VmWare tools are installed correctly on the system. |
| Base.DistributedCOMUsers.Tests | Testing local DistributedCOMUsers membership | Local DistributedCOMUsers should have only swisscom-allowed accounts as member Please remove any added users from Distributed COM Users group and follow user management procedure to give access: https://docs.entcloud.swisscom.com/guide/managed-services/managed-os-win/how-to/user-management/ |
| Base.DomainJoin.Tests | Testing the computers domain membership | The Computer should be part of a swisscom resource domain. Should computer fall off the domain, please ask support to re-join it. |
| Base.DriveFull.Tests | Testing Drive capacity | System Drive Should have minimum 20 GB of free space Data Drive Should have minimum 5 GB of free space Please free up some space, for system drive or Data drive. Run disk cleanup ( cleanmgr.exe), selecting Windows Update Cleanup can free up space, it will not be possible to uninstall updates after this action.Otherwise, please extend the disk. |
| Base.EventlogProperties.Tests | Testing if event log maximum size and -log mode are configured correctly | The log mode for Application-, System- and Securitylog should be Circular The maximum size for the Systemlog should be greater than or equal to 262'144 KB The maximum size for the Applicationlog should be greater than or equal to 262'144 KB The maximum size for the Securitylog should be greater than or equal to 524'288 KB The following commands can set the minimum acceptable limit: Limit-EventLog -LogName System -MaximumSize 262144KB -OverflowAction OverwriteAsNeededLimit-EventLog -LogName Application -MaximumSize 262144KB -OverflowAction OverwriteAsNeededLimit-EventLog -LogName Security -MaximumSize 524288KB -OverflowAction OverwriteAsNeeded |
| Base.IISLogLocation.Tests | Testing if the IIS logs are at the correct location | The IIS Logs for each website should be at the data volume, please move them away from C:\ drive by configuring Logging for each site in IIS Manager console. |
| Base.LocalAccountTokenFilterPolicy.Tests | Testing Remote UAC LocalAccountTokenFilterPolicy | The LocalAccountTokenFilterPolicy should be activated Allow local accounts of the Administrators group other than the built-in administrator account to remotely manage the server If policy is not activate, please re-activate it by setting up the registry key Set-ItemProperty -Path 'HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\system' -Name "LocalAccountTokenFilterPolicy" -Value 1 |
| Base.LoggedOnUsers.Tests | Testing Logged on Users | There should be no local users with local admin rights logged on. Please log off all users from the server and try again. |
| Base.LogMgmtInstallation.Tests | Testing installed Log Management software | The Log Management Agent Service should be running The Log Management Agent Service should be Automatic The connectivity to the Log Management server should work |
| Base.MalwareProtectionInstallation.Tests | Testing Malware Protection availability and installation | The Check initialy validates if a Supported Malware Protection Agent is installed on the system. It then continues to validate the Installation Trend Micro Deep Security Trend Micro Deep Security Agent Service should be Automatic. If it is not, please reset it to Automatic Set-Service ds_agent -StartupType AutomaticTrend Micro Deep Security Agent Service should be running. To start it up, please run Start-Service ds_agentThe connectivity to the Deep Security Manager should be in a good state Trend Micro Deep Security Agent Status should be green Trend Micro Deep Security Agent Component AM Mode should be on Agent is configured by policy, and it is not changeable from the machine. If there are problems with Trend Micro Deep Security Agent, please ensure that network connectivity is present for policy to come down: Query agent status: "C:\Program Files\Trend Micro\Deep Security Agent\dsa_query.cmd" -c "GetAgentStatus"From the output, please copy value for AgentStatus.dsmUrl. This is the management point.Ensure that dsmURL is accessible from the machine Test-NetConnection -ComputerName '{Management point hostname here}' -Port '4120' |
| Base.MonitoringInstallation.Tests | Testing installed Monitoring software | The Monitoring Agent Service should be Automatic To change service startup type: Set-Service 'End Point Operations Management Agent' -StartupType AutomaticThe Monitoring Agent Service should be running To start a stopped service, please run: Start-Service 'End Point Operations Management Agent'The Monitoring Agent should be in a good state and Operations manager endpoint should be accessible with good network connectivity. Please ensure that network connectivity exist and network round trip is less than 200ms: Find out the hostname and the port of the endpoint: Select-String -Path "$($env:ProgramFiles)\VMware\ep-agent\conf\agent.properties" -Pattern 'agent.setup.serverIP=*'Select-String -Path "$($env:ProgramFiles)\VMware\ep-agent\conf\agent.properties" -Pattern 'agent.setup.serverSSLPort=*'The following command to run network check to the endpoint: Test-NetConnection -ComputerName '{Management point hostname here}' -Port '443' |
| Base.NicPowerSaving.Tests | Testing Network Adapter Power Management | Each network interface should have Powersaving disabled. Please use the following Powershell command to disable power saving on all Network adapters attached to the machine: Get-NetAdapter -Physical | Get-NetAdapterPowerManagement | foreach {$_.AllowComputerToTurnOffDevice = 'Disabled'; $_ | Set-NetAdapterPowerManagement} |
| Base.NugetAccess.Tests | Testing Web Access to the Nuget repository | The Nugetfeed should be accessible within 100ms |
| Base.OSLanguage.Tests | Testing OS Language | The OS Language should be 'english, United States (en-US) This affects only language for Operating system User Interface, e.g. menus, messages. Keyboards layouts can be of any language and are not restricted. Swisscom does not supply multilingual UI build and also does not distribute patches for languages other than English US To confirm language for OS, please run the following command: Dism /online /Get-IntlTo change default UI language: Dism /online /set-allIntl:en-US |
| Base.OSLicenceState.Tests | Testing the Windows Licence activation | The KMS Server should be registered The name resolution for the KMS Server should return an ip address The connectivity to the KMS Server should be accessible within 100ms The OS should be licensed The OS Licence should be activated The Key Management server is found via DNS, to confirm if your configured DNS server have KMS, please run the following query: slmgr.vbs /dliIf server is resolved correctly, the output should give you KMS server IP address and port (1688) If this server is accessible, please run the following command to re-activate the machine: slmgr.vbs /ato |
| Base.OSVersion.Tests | Testing OS Version | The Server should have a Swisscom-supported OS Version Swisscom supports Windows Server 2019, Windows Server 2016 or Windows Server 2012 R2 |
| Base.PageFileSettings.Tests | Testing PageFile Configuration | The Server should have PageFile manually managed Page file Initial size should be equal or greater then 4'096 MB Page file Maximum size should be equal or greater then 4'096 MB. To set pagefile to minimal acceptable limits, please run the following command: wmic pagefileset where name="C:\\pagefile.sys" set InitialSize=4096,MaximumSize=4096 |
| Base.PerformanceMonitorUsers.Tests | Testing local PerformanceMonitorUsers membership | Local PerformanceMonitorUsers should have only swisscom-allowed accounts as member Please remove any added users from Performance Monitor Users group and follow user management procedure to give access: https://docs.entcloud.swisscom.com/guide/managed-services/managed-os-win/how-to/user-management/ |
| Base.RegistryRunKeys.Tests | Testing entries in Run and RunOnce | Run, RunOnce, RunServices, RunServicesOnce should not have any subkeys. Please analyse the following keys to ensure there are only allowed entries there: HKLM:\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\RunServices HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\RunServicesOnce HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Run HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce By default, only the these entries are allowed: Deep Security Notifier InstallWindowsUpdates" VMware VM3DService Process VMware User Process |
| Base.RemoteDesktopProtocol.Tests | Testing Remote Desktop Protocol Settings | The remote desktop connections should be enabled in 'HKLM:\System...' The remote desktop connections should be enabled in 'HKLM:\SOFTWARE\Policies...' To enable this, please set the following registry key with the Powershell: Set-ItemProperty -Path 'HKLM:\System\CurrentControlSet\Control\Terminal Server' -name "fDenyTSConnections" -value 0The firewall rule 'RemoteDesktop-UserMode-In-TCP' should be enabled, to enable it, please use the following Powershell Command: Enable-NetFirewallRule -Name RemoteDesktop-UserMode-In-TCPThe firewall rule 'RemoteDesktop-UserMode-In-UDP' should be enabled, to enable it, please use the following Powershell Command: Enable-NetFirewallRule -Name RemoteDesktop-UserMode-In-UDP |
| Base.RemoteDesktopUsers.Tests | Testing local RemoteDesktopUsers membership | Local RemoteDesktopUsers should have only swisscom-allowed accounts as member Please remove any added users from Remote Desktop Users group and follow user management procedure to give access: https://docs.entcloud.swisscom.com/guide/managed-services/managed-os-win/how-to/user-management/ |
| Base.Services.Tests | Testing if unnecessary services are disabled | The following Services should be disabled - AudioEndpointBuilder - Audiosrv - Browser - FontCache - iphlpsvc - NcaSvc - NetTcpPortSharing - RemoteAccess - SCardSvr - seclogon - SharedAccess - ShellHWDetection - SSDPSRV - Themes - upnphost - WcsPlugInService To disable all these services at once, please use the following Powershell command: @('AudioEndpointBuilder', 'Audiosrv', 'Browser', 'FontCache', 'iphlpsvc', 'NcaSvc', 'NetTcpPortSharing', 'RemoteAccess', 'SCardSvr','seclogon','SharedAccess', 'ShellHWDetection', 'SSDPSRV', 'Themes', 'upnphost', 'WcsPlugInService') | foreach {Set-Service -Name $\_ -Status stopped -StartupType disabled} |
| Base.SNMPWriteCommunity.Tests | Testing SNMP Write Community String | There should be no SNMP Write Communities defined. Please ensure, there is nothing defined under this registry key: SYSTEM\CurrentControlSet\Services\SNMP\Parameters\ValidCommunities\ |
| Base.StickyKeyBackdoor.Tests | Testing for Sticky Key Backdoors | The hash value of Ease of Access system files should meet the OS version Scan each of those files to ensure they have not been maliciously replaced: sfc /verifyfile=C:\Windows\System32\sethc.exesfc /verifyfile=C:\Windows\System32\utilman.exesfc /verifyfile=C:\Windows\System32\osk.exesfc /verifyfile=C:\Windows\System32\utilman.exesfc /verifyfile=C:\Windows\System32\Magnify.exesfc /verifyfile=C:\Windows\System32\Narrator.exesfc /verifyfile=C:\Windows\System32\DisplaySwitch.exeEase of Access system files should not be have a debugger for hijacking the system Remove Debug key, by running the following Powershell command: |
| Base.SwisscomCertificate.Tests | Testing Swisscom Root Certificates | There should be Swisscom Root certificates available The Swisscom Root certificates should be valid |
| Base.UnsupportedSoftwareInstalled.Tests | Testing if unsupported software is installed | The following Features/Software should not be installed: - Active Directory Domain Services - SAP - SharePoint - Exchange The DB directory of the following Databases should not be on the system disk: - Microsoft SQL Server - MySQL - MongoDB - Oracle - MariaDB - PostgreSQL The current version of the following Applications should be greater or equal than: - Java Version 1.8.0 - OpenJDK Version 1.8.0 - Apache Tomcat Webserver 8.5 - Microsoft SQL Server 12.0 (MS SQL Server 2014) The installation directory of the following Applications should not be located on the system disk: - Apache Tomcat Webserver - JBoss |
| Base.VMTools.Tests | Testing VMware Tools | The 'VMware Tools' Service should be running, please use the following command to start the serviceStart-Service 'VMTools'The 'VMware Tools' Service should be Automatic, please useservice the following command to set service startup type to Automatic Set-Service 'VMTools' -StartupType AutomaticThe VMware Tools should be up to date |
| Base.WindowsFirewall.Tests | Testing Windows Firewall | The 'MpsSvc' Service should be running, please use the following command to start the serviceStart-Service 'MpsSvc'The 'MpsSvc' Service should be Automatic, please useservice the following command to set service startup type to Automatic Set-Service 'MpsSvc' -StartupType AutomaticAll Windows Firewall profiles should be enabled The firewall rule for File and Printer Sharing (SMB-In) should be enabled, to enable it, please use the following Powershell Command: Enable-NetFirewallRule -DisplayName 'File and Printer Sharing (SMB-In)' |
| Base.WindowsManagementFramework.Tests | Testing installed Windows Management Framework | Windows Management Framework version 5.1 should be installed |
| Base.WindowsPatching.Tests | Testing Windows Patching | The difference between the last Windows updates should not be more than 45 days |
| Base.WindowsRemoteManagement.Tests | Testing Windows Remote Management | The 'WinRM' Service should be running, please use the following command to start the serviceStart-Service 'WinRM'The 'WinRM' Service should be Automatic, please use the following command to set service startup type to Automatic Set-Service 'WinRM' -StartupType AutomaticThe WinRM Listener should be active The firewall rule 'WINRM-HTTP-In-TCP' should be enabled, to enable it, please use the following Powershell Command: Enable-NetFirewallRule -Name WINRM-HTTP-In-TCPThe firewall rule 'WINRM-HTTP-In-TCP' should be Allowed |
| Base.WindowsUpdate.Tests | Testing Windows Update | The 'wuauserv' Service should not be Disabled Please do not disable Windows Update service, if it is disabled, please set it back to Automated (Delayed Start): sc.exe config wuauserv start= delayed-autoThe connectivity to the Update Server should be in a good state |
Run Compliance Checks manually
Managed Windows
The compliance checks for Managed Windows OS on Swisscoms ESC are run using a custom build framework called PccComplianceChecks or PCC for short.
Each time a compliance check is run, the PCC is called behind the curtains and it triggers a so called PccRun.
A PCCRun is the operation that runs when an Exit Temp Admin is launched in the Portal or system is returned to Full Managed mode for instance.
A PccRun executes a number of infrastructure related tests to validate the OS running in the VM is compliant with Swisscoms Managed OS standards. The module has been made publicly available so that compliance checks can be run locally on the Swisscom Windows OS.
PCC is locally available to ESC customers starting with version 1.0.0 of the PccComplianceChecks package.
Why use PCC manually
Executing an ExitTempAdmin or Return to Full Managed mode via the regular Day 2 Action can last a few minutes and potentially result in failing checks that need to be corrected. To simplify and to speed up this process, it is now possible to call the same tests that run during the Return to Full Managed mode but directly on your VM.
The main benefit of doing so is the gain in time in validating that the OS is Swisscom standards conform before executing the Return to Full Managed action.
With PCC, it is also possible to get a history of the past runs.
Verify the local PCC version
IMPORTANT NOTE: To download and install the latest versions of the PCC Framework and the required module "PCC.CHK.ESC.WIN.MOS" locally, we recommend to execute first an "Exit Temp Admin" or "Return To Full Managed" Day 2 Action in the ESC Portal.
Open a PowerShell prompt and execute the following PowerShell command(s):
This request is used to get the current version of PCC working on your Managed Windows OS.
Request
Get-Module PccComplianceChecks -ListAvailable
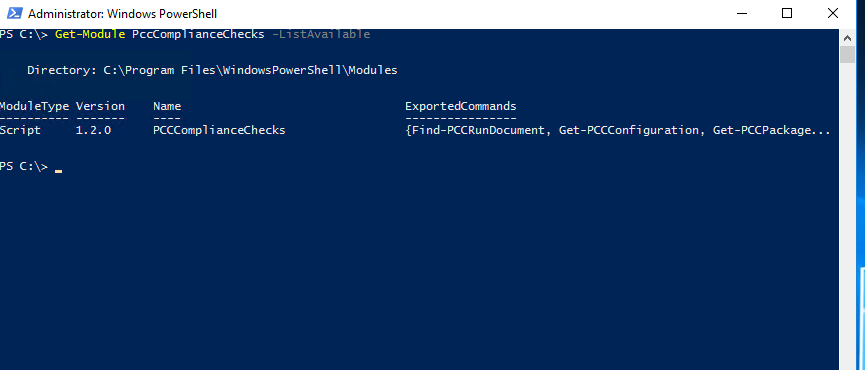
Note: One or more different PCC versions can co-exist on the same machine. The one with the highest version number is the latest version available.
Execute a PCCRun
Open a PowerShell prompt and execute the following PowerShell command(s):
Only messages of the failed checks will be displayed on screen. If none are shown, it means that the Managed Windows OS is compliant.
Request
Test-TempAdmin
Alternatively, it is possible to output directly the run using the following snippet.
Request
Test-TempAdmin -ShowRun
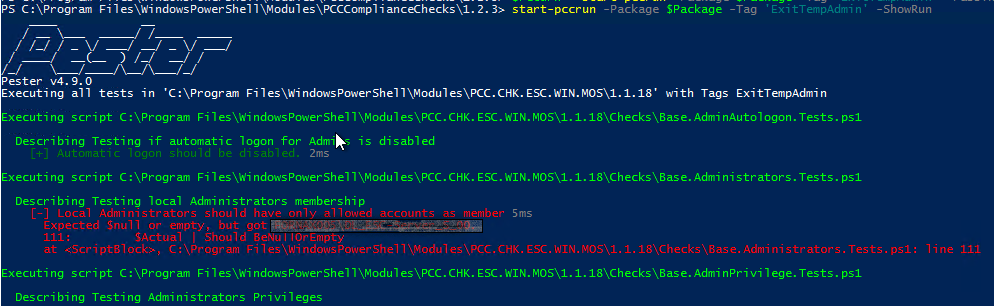
Get all past PCC run results
NOTE: Results can only be retrieved from compliance checks that have run using the PccComplianceChecks version 1.2.0 or above. Any run done with a previous version will not generate the needed PccRunDocument.
Open a PowerShell prompt and execute the following PowerShell command(s):
Request
Get-PccRundocument
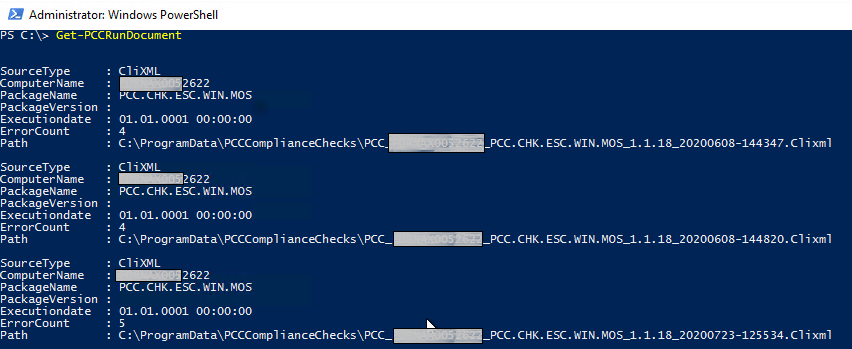
Note: The 'ErrorCount' property indicates how many compliance checks have failed during that specific run.
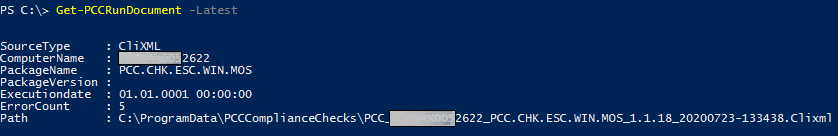
Results will look similar to the screen shot below but will vary according to the VM and its current compliance.
Request
Get-PccrunDocument -Latest
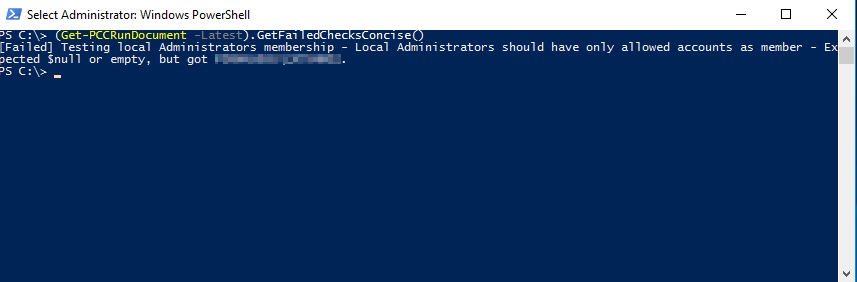
To get the list of the failed checks from the last PCC run (or failed Return to FullAdmin) execute the following code. Results will look similar to the screen shot below but will vary according to the VM and its current compliance.
Request
(Get-PCCRunDocument -Latest).GetFailedChecksConcise()