Overview
The Managed RHEL service enables you to transfer Operating System tasks in the Enterprise Service Cloud environment to Swisscom. This includes antivirus protection, patching and monitoring of the base Operating System parameters (monitoring and alarming), as well as incident management. The use of Managed RHEL components meets high-quality requirements and is suitable for business-critical applications.
The Managed RHEL service is characterized by the following features: Swisscom ensures the secure and reliable operation of the Operating System environment and thus enables the customer to use IT resources at the application level.
Main changes for Managed RHEL v2 compared to Managed RHEL
- Improved Disk Management. All disk and filesystem manipulations can be done in the portal.
- Patching of Managed RHEL v2 VMs also in the Temp Admin state at the selected patch window!
- Immediately apply custom iptables/nftables rules with a service restart.
- The payload for executing actions via API has changed.
- Configuration Management is done with Ansible instead of Puppet.
Prerequisites and basic conditions
The Managed RHEL service can be ordered for the following Operating Systems and versions:
- Red Hat Enterprise Linux RHEL 8
- Red Hat Enterprise Linux RHEL 9
To guarantee the services of Managed RHEL, a few basic conditions for Managed RHEL must be considered.
This will ensure that the operation team can take over the responsibility for the Managed RHEL systems.
Please note the basic conditions below, before you install or configure an application on a Managed RHEL VM.
To ensure that the basic conditions for a Managed RHEL VM are met, a Compliance Check will be used. This check is executed whenever a Managed RHEL VM is being transferred to the Full Managed state.
The details of the checks which are carried out can be found in the Technical Description.
These are the most important basic conditions which apply for Managed RHEL:
- Managed RHEL is not suitable for container services like Docker, Openshift, etc. because of the difficult separation of responsibilities between the Operating System, the application and container services.
- The Operating System is configured with Ansible. The Operating System configurations are enforced regularly. It should not be attempted to overwrite this configuration with a scheduled job.
- All additional software, which will be installed, must be installed on additional disks. Also, all application related logfiles must be written to a partition on an additional disk. All partitions created during VM provisioning are reserved for the Operating System. These partitions are monitored by the operation team and therefore may not be used for the application software and application logs.
- For Managed RHEL 8 the firewall service
iptablesmust run, additional rules must be configured in the/etc/sysconfig/iptables.customfile. You can activate the custom rules with a restart of the iptables service. Starting with Managed RHEL 9 usenftablesinstead of iptables. You can configure custom rules in/etc/nftables/mos-lnx-customer-chains.nftand/etc/nftables/mos-lnx-customer-nat-chains.nftand then restart thenftablesservice for activating the custom rules. - SELinux must be running and active in the permissive mode.
- No cronjobs are allowed for the user root. Only the operation team can configure cronjobs with privileged permissions.
- No additional processes are allowed which run under the user root.
- Sudo rule must be ordered via service request. This ensures that the operation team can control which rules are ordered and can take over the responsibility for the Managed RHEL systems.
Further prerequisites and general conditions are described in the Technical Description.
Extensions
When ordering a Swisscom RHEL VM, it is possible to activate extensions. By activating the extensions, additional features are configured when creating the Swisscom RHEL VM, which turn an unmanaged Swisscom RHEL VM into a Managed RHEL VM.
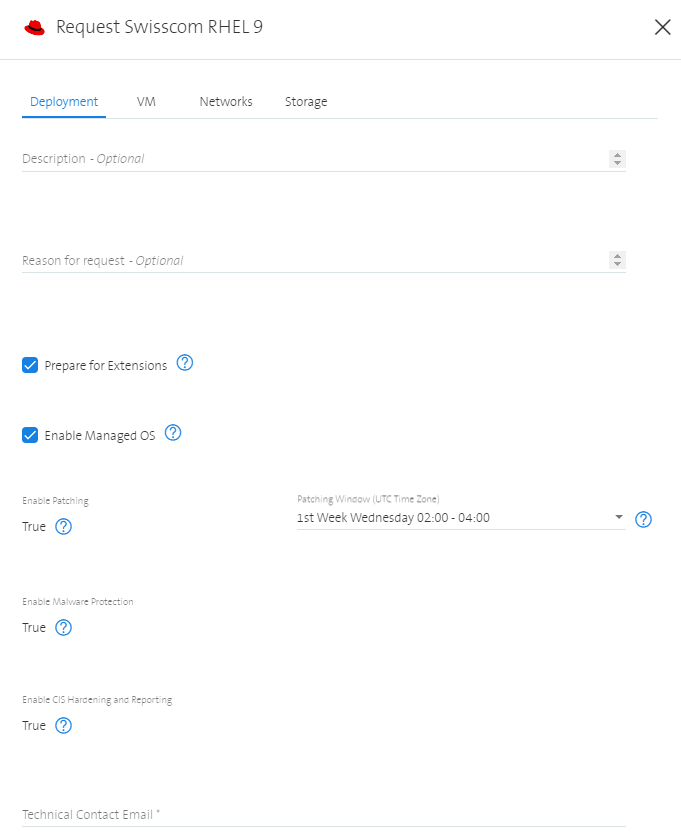
The following extensions can be selected at the moment:
Prepare for Extensions
This will prepare the VM for the usage of the configuration management tool. A dedicated service user is created and the required sudo permissions are configured. This is always needed as a prerequisite for the Managed RHEL service.
Enable Managed OS
If this extension is switched on, the Operating System is configured according to Swisscom standards so that the operation can be taken over by Swisscom. In addition, the extensions Patching, Malware Protection and CIS Hardening and Reporting are also switched on implicitly. All these extensions are necessary for the Managed RHEL service.
Service States
A Managed RHEL VM can be set to different service states. Depending on the service state, you have different rights and responsibilities. For Managed RHEL we differentiate between the following service states:
- Full Managed
- Provider Maintenance
- Customer Maintenance
- Temp Admin
For more information about the service states, see the Technical Description.
Full Managed
Swisscom is responsible for the server.
The customer has no administration or root permission on the Operating System. This should be the default state for a Managed RHEL VM. Otherwise, the VM has no SLA and Monitoring.
Provider Maintenance
Swisscom is responsible for the server.
The customer has no administration or root permission on the Operating System. Swisscom can carry out maintenance work on the server. This status is used especially during the Operating System patching to avoid disturbing influences during patching. It is not possible for the customer to switch into this state. For the customer it is not possible to execute any actions within the portal for this VM.
Customer Maintenance
The customer is responsible for the server.
- No Service-Level Agreements (SLA) guaranteed.
- No Operating System monitoring provided.
In this state, the customer can perform certain actions (e.g. reconfigure, reboot or shut down the server) without having to switch to the Temp Admin state. The Service Level Agreements at OS level are suspended in this state.
Temp Admin
The customer is responsible for the server.
- No Service Level Agreements (SLA) guaranteed.
- No Operating System monitoring provided.
- As of Managed RHEL v2, the VM is also automatically patched in the Temp Admin state at the selected patch window!
The customer receives temporary administration or root permissions on the Operating System. The Service Level Agreements at Operating System level are suspended in this state. This state should only be a temporary state. The VM should be switched back to the Full Managed state as soon as possible!
Service Level
The following service levels are provided for the Managed RHEL service.
| Basic | Standard | Advanced | |
|---|---|---|---|
| Support Time | Mo - Fr 07:00 - 18:00 | Mo - Sun 00:00 - 24:00 | Mo - Sun 00:00 - 24:00 |
| Service Availability | 99.5% - Operating System | 99.9% - Operating System | 99.9% - Operating System |
| ICT Service Continuity | RTO Best Effort - RPO Best Effort | RTO Best Effort - RPO Best Effort | RTO 4 h - RPO Near to 0 |
- The service level variants Basic, Standard and Advanced are selectable when ordering a Managed RHEL blueprint.
- The Advanced service level variant contains the service continuity services at VM respectively Operating System level. Neither recovery at application level nor its regular failover tests are part of this service.
