Configure Identity Provider (IdP)
OpenID Connect (OIDC) user authentication can be configured on the Kubernetes API Server using the Day 2 Action "Edit Cluster".
OIDC cluster settings
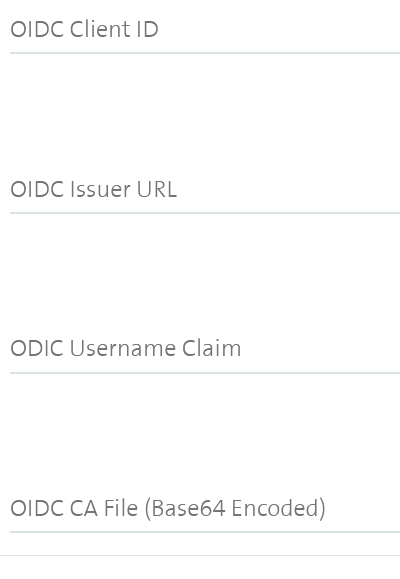
- OIDC Client ID: An arbitrary client id that all tokens must be issued for, e.g. "kubelogin" or "kubernetes".
- OIDC Issuer URL: Provider's discovery URL (usually without a path), for example "https://accounts.google.com" or "https://dex.mycompany.ch".
- OIDC Username Claim: JWT claim to use as the user name. By default
sub, which is expected to be a unique identifier of the end user. Admins can choose other claims, such asemailorname, depending on their provider. However, claims other thanemailwill be prefixed with the issuer URL to prevent naming clashes with other plugins. - OIDC CA File (Base64 Encoded): CA that signed your identity provider's web certificate, needs to encoded with base64 without newslines, e.g.
cat ca.pem | base64 -w 0
OIDC Provider
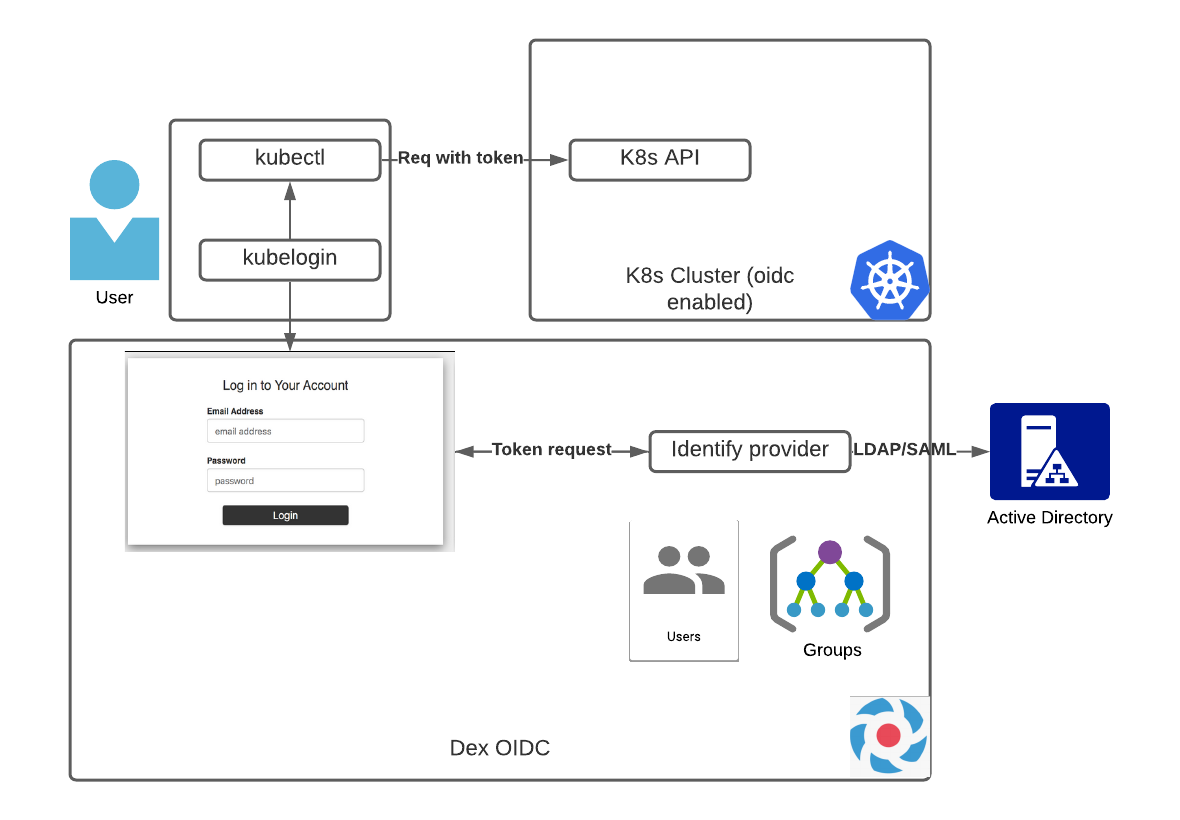
A OIDC Provider must be available to use your Identity Provider (e.g. Active Directory) as the backend for Kubernetes Authentication. It is possible to set up a OIDC provider like dex or keycloak on a TKGI cluster for other K8s clusters for user authentication.
This OIDC provider can be exposed as service type Loadbalancer or via Ingress. The CA certificate used to expose it then needs to be set on the client K8s cluster via "OIDC CA File".
Please find an example configuration on the dex github.
Kubectl
To facilitate the token process on the client side we suggest using the kubectl plugin kubelogin.
Please find an example configuration (kubelogin+dex+active directory) on the dex documentation.
OIDC example setup